A customer was trying to harden its Windows 2008 R2 server, based on findings from SSL Test that recommends he disable any use of SSL 2.0 and TLS 1.0 on IIS server.
The problem is that once you restrict these protocols, you will almost certainly break RDP.
On the server Event Viewer you will see the following event from the Scannel source:
A fatal error occurred while creating an ssl server credential. The internal error state is 10013
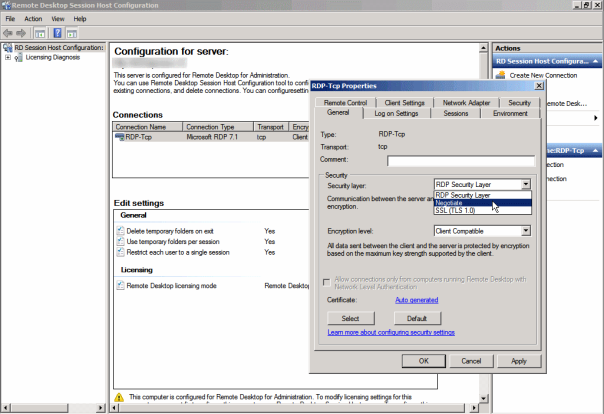
By default, Windows 2008 R2 remote desktop host is configured to Negotiate the use of either its internal RDP Security Layer OR the SSL/TLS 1.0. In this mode both RDP client and server fallback to a protocol they both support.
Please check the setting under: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server\
If Enabled=0 than you have found the source to the problem. But not the reason…
The reason is that the Negotiate settings in Remote Desktop server doesn’t really work… What you need to do is EXPLICITLY select the “RDP Security Layer” under the Security section of the General Tab of the Remote Desktop Session Host Configuration (see picture)